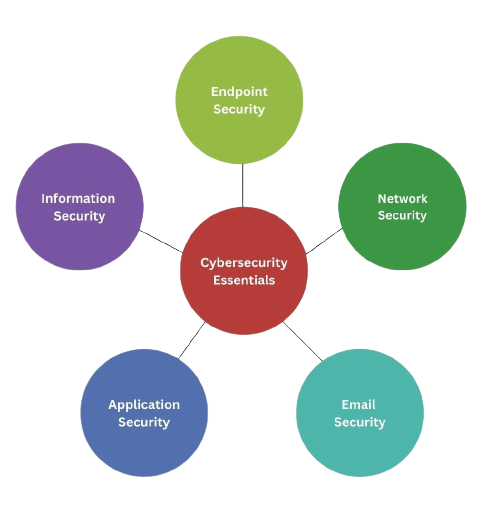
Your Cyber Security With a Trusted Provider
There are 30,000 web sites hacked each day - yes each day - 43% Of attacks are targeted as small to medium businesses. Every business that is connected to the internet is a target to hackers. Just having email spam software doesn't prevent you being hacked. Your Data is a valuable asset - how would you feel if it was hacked and sold to criminals , especially your clients details. BizSoft Cyber - is part of BizSoft International Group, we are here to help you understand what Cyber Risks your business may have & help you in implementing the best security prevention program.
Overall IT
Take this quick check up of your Overall IT Risk status